BabyAndroid
常规,JEB反编译
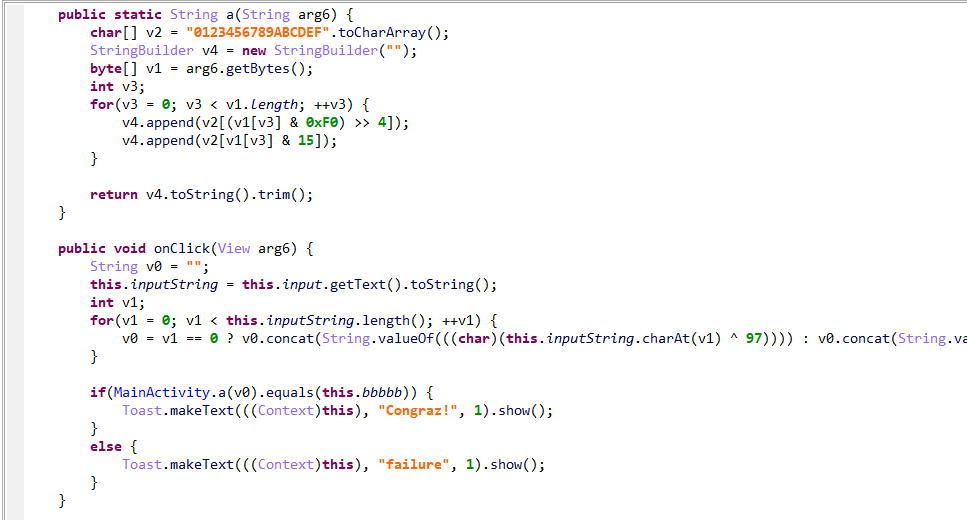
根据输入的字符串长度,第一位和97异或,后面跟v0的字符异或,把结果字符串转入a函数中。a函数首先把给出的常量字符串转为数组,把传入的字符串转化为bytes数组,再根据数组长度把每一位做for中&和左移计算,结果为3267347723651E492C1D7E117C1946325D02432D493B0B62067B则为真。所以逆推,由于一次计算拼接两位,所以按照两位为一个字符计算。其中含有字母,调试得知是对应的十六进制数。
#coding:utf-8
strs = "3267347723651E492C1D7E117C1946325D02432D493B0B62067B"
num = []
for i in range(0, len(strs)):
num.append(strs[i]) #52
nums = []
id = 0
while id < 52:
for i in range(0,200):
if str((i & 0xF0) >> 4) == num[id]:
if hex(i & 15).replace('0x','').upper() == num[id+1]:
nums.append(i)
break
id = id + 2
flag = []
for i in range(0, len(nums)):
if i == 0:
first = nums[i] ^ 97
flag.append(first)
else:
sc = nums[i] ^ nums[i-1]
flag.append(sc)
text = ''
for i in flag:
text = text + chr(i)
print(text)
>>> SUSCTF{We1come_to_Andr0id}后来看了其他资料,才发现a函数下面的for循环就是找16进制对应的十进制数,如
>>> int('32',16)
50
其中是利用50找到对应的十进制32.这个点卡了N久,看到一份别人的poc写的是相当简洁了。
CrackMe
又是一个native层的APP。
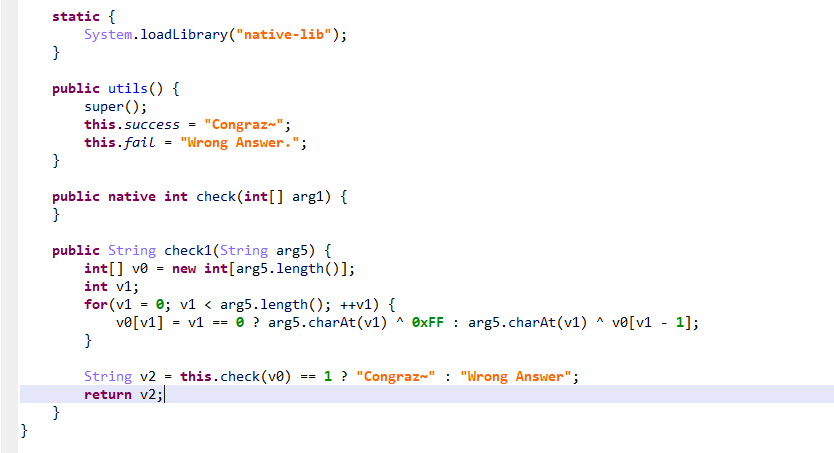
IDA打开伪代码
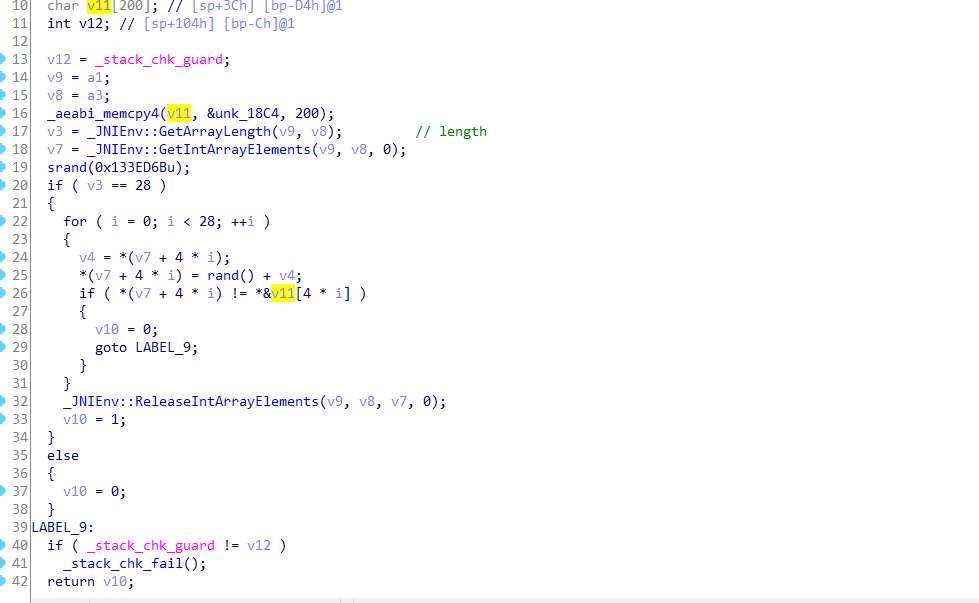
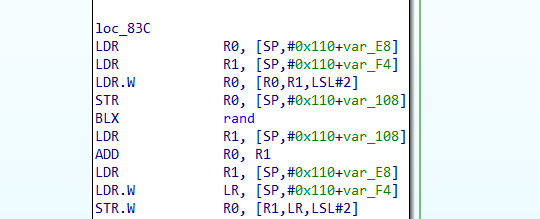
根据汇编得知,中间for循环处操作的是数组
其中v11是给出的数据块,按照int型,四位一个字段,正好28个字段。
按照Java层逻辑和伪代码写出c代码为
#include <stdio.h>
#include <stdlib.h>
int main(){
int v11[28] = {0x571a9693,0x23a96034,0x6a943d8c,0x1f9222ed,0x73887c81,0x5c13a257,0x26407522,0x13646a3a,0x2139537f,0x35415c5f,0x321304b7,0x238a8c26,0xd7307f6,0x622d5268,0x7c3d2e04,0x72198f7e,0x7df76af2,0x4e8431aa,0x28650861,0xfd8e3e9,0x196c1f1a,0x5fe8ab3,0x1231495d,0x5359d998,0x35fcfde0,0x3b2d0dd4,0x61113e45,0x314c57b8}; //小端字节序
int v0[28] = {0};
int string[28] = {0}; //未定义,引入的参数变量
int i;
for (i=0; i<28; i++){
if (i == 0){
v0[i] = string[i] ^ 0xFF;
}
else{
v0[i] = string[i] ^ string[i-1];
}
}
srand(0x133ED6B);
int v4[28] = {0};
for (i=0; i<28; i++){
v4[i] = v0[i] - rand();
if (v11[i] != v4[i]){
int v10 = 0;
return v10;
}
int v10 = 1;
printf("%c",v10);
return v10;
}
}也就是我们需要反向求出string的值
#include <stdio.h>
#include <stdlib.h>
int main(){
int v11[28] = {0x571a9693,0x23a96034,0x6a943d8c,0x1f9222ed,0x73887c81,0x5c13a257,0x26407522,0x13646a3a,0x2139537f,0x35415c5f,0x321304b7,0x238a8c26,0xd7307f6,0x622d5268,0x7c3d2e04,0x72198f7e,0x7df76af2,0x4e8431aa,0x28650861,0xfd8e3e9,0x196c1f1a,0x5fe8ab3,0x1231495d,0x5359d998,0x35fcfde0,0x3b2d0dd4,0x61113e45,0x314c57b8};
int v0[28] = {0};
srand(0x133ED6B);
for (int i=0; i<28; i++){
v0[i] = v11[i] - rand();
}
int string[28] = {0};
for (int i=0; i<28; i++){
if (i==0)
string[i] = v0[i] ^ 0xFF;
else{
string[i] = v0[i] ^ v0[i-1];
}
}
for (int i=0; i<28; i++){
printf("%c", string[i]);
}
return 0;
}但是尴尬的是算出来的是乱码
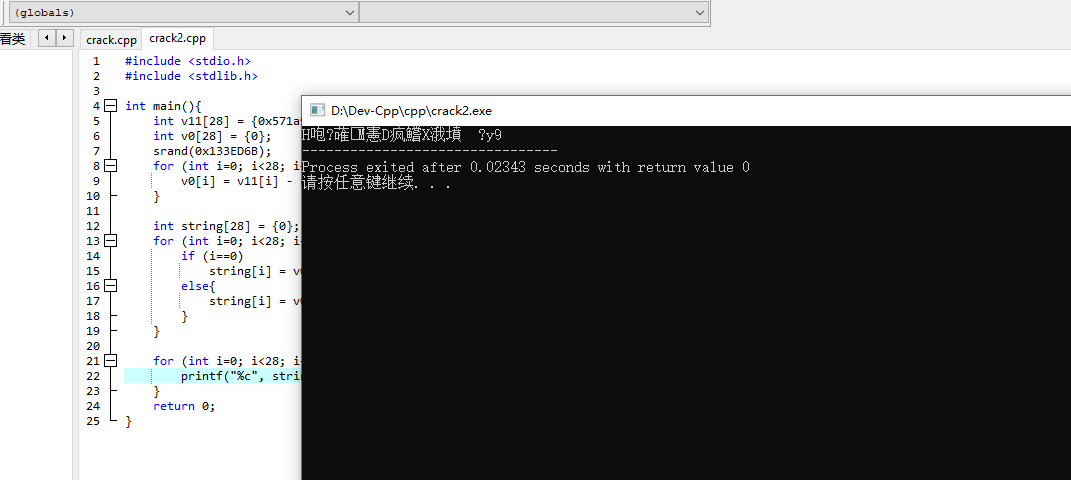
然后没有找到这题的wp….也没找到其他问题的存在点。就这样吧,毕竟是汇编渣渣。